In 2011, the Ponemon Institute estimated that the worldwide education and research sector spends nearly $7 million annually to comply with privacy and security regulations. Since then, we’ve witnessed a rising tide of state data privacy and security breach notification laws. These laws are meant to improve the privacy and security of major business, health, P-12, and higher education institutions through compliance and have almost certainly played a role in increasing these costs. We can see that legislators are trying to regulate privacy and security practices and educational institutions are working to comply. Despite these recent efforts, however, we’ve also seen a number of highly publicized data breaches.
Understandably, higher education stakeholders are very focused on ensuring that their technology systems are secure and their data is private. Most view compliance with new legislation as a way to lessen the risks of breaches, litigation, fines, and loss of funding. While they see the value in compliance, many of the colleges and universities we work with find that it is far from straightforward. In fact, most find it difficult to even identify which laws apply to them.
Among existing federal laws, only the Family Educational Rights to Privacy Act (FERPA) explicitly applies to postsecondary institutions. The remaining privacy- and security-related federal laws may only apply based on the institution’s activities and the data it stores. For example, the applicability of the Health Insurance Portability and Accountability Act (HIPAA) to an institution depends on whether it serves as “a healthcare provider that conducts covered transactions electronically.” Similarly, the applicability of the Payment Card Industry Data Security Standards (PCI DSS) depends on whether an institution receives students’ credit card information. Likewise, the applicability of the Gramm-Leach-Bliley Financial Services Modernization Act (GLB) depends on whether an institution manages its own student financial aid programs as a financial institution.
Of the 28 states that passed security-related laws in 2015, only Illinois identified its higher education institutions. There are currently more than 50 proposed state security-related laws on topics such as data privacy, access to social media passwords, and security breach notifications, none of which explicitly identify higher education.
Finding Your Way
There are a number of possible approaches to compliance, including security frameworks that tend to be more heavy and top-down. Before adopting one of these approaches, we propose the following steps to help you devise a tactical approach to complying with the legislation that applies to higher education:- Assign ownership and accountability for legislative knowledge management. Given the sheer amount of legislation in place, the first step is to assign responsibility for collecting, analyzing, storing, and tracking all legislation. Baylor University, for example, has appointed a vice president of compliance and risk for this purpose. The University of Wisconsin is investigating the use of a governance, risk, and compliance tool.
- Convene a cross-functional team to determine legislative applicability. While it is important to have an information technology governance team to lead, organize, and operate your institution’s IT programs, delaying your compliance review until this team is formulated may delay your institution’s ability to reach full compliance. Consider creating a joint team of legal, technology, and privacy stakeholders to review collected legislation together and determine which legislation is applicable.
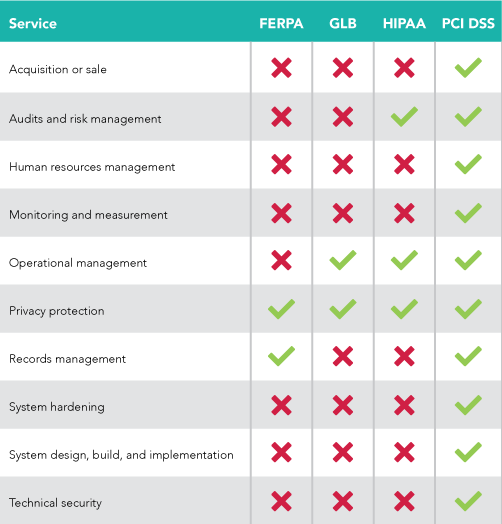
- Review legislation against institutional data and services. Once it has been determined that a given piece of legislation applies to your institution, determine which data types and technology-related services it covers. For example, the University of Michigan developed a thorough review process to determine which data types and services are covered by all applicable legislation. Another approach is to leverage the control categories identified in some security frameworks to determine which are covered by a given piece of legislation, as shown in the table below.

- Review vendor contracts against applicable data and services. As we have previously written, institutions can take key steps to providing oversight of vendor products. Further, review the vendor contracts and processes to ensure that they adhere to the data and services covered in a given piece of legislation. This is critical because, in most cases, the institution is more “on the hook” for non-compliance than the vendor. Lastly, in cases when it is not clear whether a vendor truly adheres to the covered data and services, institutions should consider adding contractual requirements to ensure adherence. These might include disaster and recovery plans or penetration and vulnerability testing.

