Drawing on Eduventures’ 20-plus years of experience helping universities develop, launch, and assess academic programs, the Program Spotlight Series of Wake-Up Calls calls attention to best practices in program development.
By now it’s an open secret that cybersecurity is a hot ticket in the world of academic programs. Employment prospects for graduates are excellent—many employers can’t fill open positions fast enough. Many institutions have added, or are thinking about adding, a new cybersecurity program to their portfolios. Since we last took the pulse of this market in our cybersecurity webinar two years ago, this academic field has successfully shed its niche existence and entered mainstream. It is time to take stock and re-examine what we know about it: What is the status quo, and where is this field going? Is it starting to become saturated? How is it evolving?
By now it’s an open secret that cybersecurity is a hot ticket in the world of academic programs. Employment prospects for graduates are excellent—many employers can’t fill open positions fast enough. Many institutions have added, or are thinking about adding, a new cybersecurity program to their portfolios. Since we last took the pulse of this market in our cybersecurity webinar two years ago, this academic field has successfully shed its niche existence and entered mainstream. It is time to take stock and re-examine what we know about it: What is the status quo, and where is this field going? Is it starting to become saturated? How is it evolving?
Competition is growing by the minute, but…
We have started hearing anecdotes of increasing competition and the start of market saturation – is this true? Figure 1 below plots conferral growth across all degree levels against provider growth.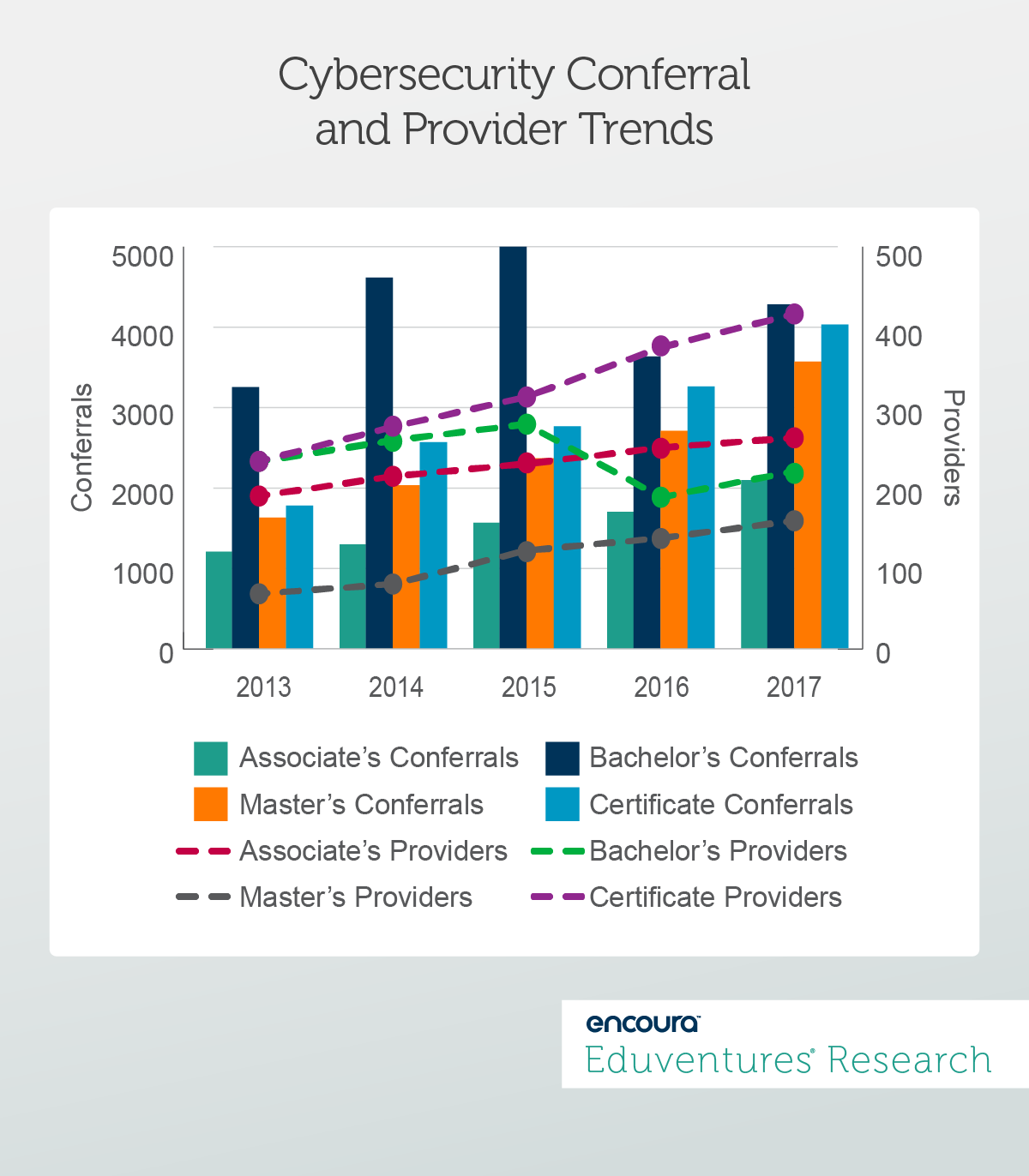
Evolution: From Policing to Managing
While institutions are busy churning out graduates with just enough programming and ethical hacking skills to land jobs, the cybersecurity industry as a whole is changing as it reacts to new threats and new challenges. To put it in the context of the NIST Cybersecurity Framework, it's shifting its focus from “detect,” “respond,” and “recover” functions to “identify” and “protect.” Another challenge is the increased focus on data privacy. How many times in the recent past have you encountered a pop-up message in your browser asking you to review and agree to a website’s cookie policy? Along with these trends comes the need for professionals who not only react to immediate threats but are able to anticipate and plan for potential risks, and develop policies and procedures to manage all things related to data privacy and security. These increased responsibilities require a more sophisticated, nuanced, and differentiated skillset than the average “white hat” or ethical hacker would provide. In other words, the cybersecurity industry is maturing. While higher education institutions and boot camps are still pushing graduates with rudimentary-to-advanced programming skills into the market to meet tactical needs, a new league of cybersecurity professionals is developing: the strategist. We see a growing professionalization in this market as it moves from hackers in hoodies to professionals who can shape the fundamental building blocks of their respective industries. Figure 2 below shows the gap in common skills that was listed in job postings for cybersecurity positions over a 12-month period compared to how frequently these skills were listed in workforce profiles posted on sites such as LinkedIn or Indeed.com by cybersecurity professionals over the same time period.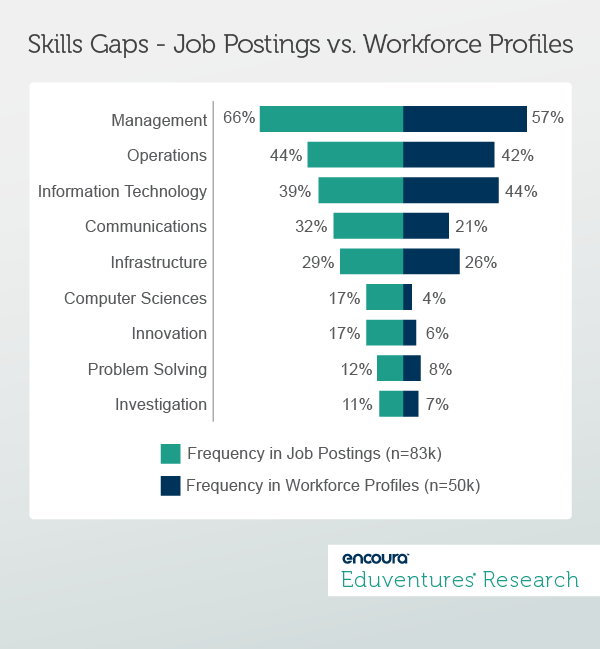
The Bottom Line
It is unlikely that demand for ethical hackers and other technically-focused roles is dwindling in the near future, but these roles are not immune to automation. Higher education institutions are also competing with alternative providers such as boot camps in this arena. For now, this market looks promising for providers based on historic growth patterns, the impact of ITT Tech’s closure in the market, and changing labor market demands that open new opportunities for forward-looking institutions. Those who take note of the changing tides in this market and the new skills demanded by employers are likely to emerge, or remain, on top. Cybersecurity is no longer just for (current and aspiring) computer geeks. The field is maturing and diversifying. In other words, cybersecurity is growing up. Thursday, January 24, 2019 at 2PM EST/1PM CST A decade ago, the enrollment management community had high hopes for social media. Facebook was an emerging communication channel, and along with MySpace, was strongly competing for members. Together, they were widely regarded as the potential magic bullet to reaching and recruiting traditional-aged prospective students. Since then, Facebook and Twitter have become household names among all age groups. But how much emphasis and budget should you put toward social media or does it work best when used as one of several key supporting elements of a balanced digital channel strategy? Data from Eduventures® Student Sentiment Survey™, featured in this webinar, identifies important opportunities for creating an effective digital strategy that includes social media. Join us on a webinar to learn:- The groups that are most responsive to social media as a means for engaging with higher ed institutions
- Why social needs to be a portion of a larger digital strategy
- How you can leverage mobile-based digital marketing to enhance your reach
- Practical application strategies you can employ today

